An online environment faces many threats today, with Distributed Denial-of-Service (DDoS) attacks being a significant concern. Depending on their goals, attackers may attempt to compromise systems or knock them offline, and a DDoS attack against an online service can be just as detrimental to business as a system breach.
What is the impact on your organization when your service becomes unavailable? We evaluate your online environment against various applicative and volumetric DDoS attacks, assessing the effectiveness of your infrastructure's security measures to ensure robust protection.
Validating Service Resilience
A Denial-of-Service (DoS) attack is an attempt to make a resource unavailable for end-users. A Distributed Denial-of-Service (DDoS) attack leverages a large number of machines to do so. Attackers will use botnets, a collection of infected computers, to achieve this.
What are your company's crown jewels, and are they adequately protected against these DDoS attacks? What might happen if your organization's services go down for one minute, hour, or day?
Getting consistent results
Building on our security intelligence capabilities, we created a Splunk-based command-and-control (C2) platform with a library of standard and custom attacks that mimic real-world attack vectors. The attack environment is scalable to your demands, and new attack bots can be added within minutes. For an optimal outcome, we configure attacks in detail to ensure they mimic real-world attacks as much as possible. These attacks can be combinations of both volumetric and application-level attacks. Using a structured approach provides a way to conduct a denial of service simulation in a fully controlled fashion. This gives you the advantage of knowing that all tests are controlled, repeatable, and comprehensive.
What do we offer
Our approach includes a preparation phase in which attack vectors of the target environment are analyzed, and a plan of attack is defined and accepted. Based on the preparation phase, the attacks will then take place in an agreed-upon timeframe and are strictly controlled. To keep you informed and involved, the attack sessions are interactive, so you don't merely receive a report after the fact but know what's going on firsthand. This way, we ensure that your operational and security monitoring teams can:
-
Validate whether controls are working.
-
Check if monitoring solutions properly identify problem areas.
-
Run through their incident response procedures.
If desired, these actions can be taken while an attack is running, so immediate results will be seen by the blue-team.
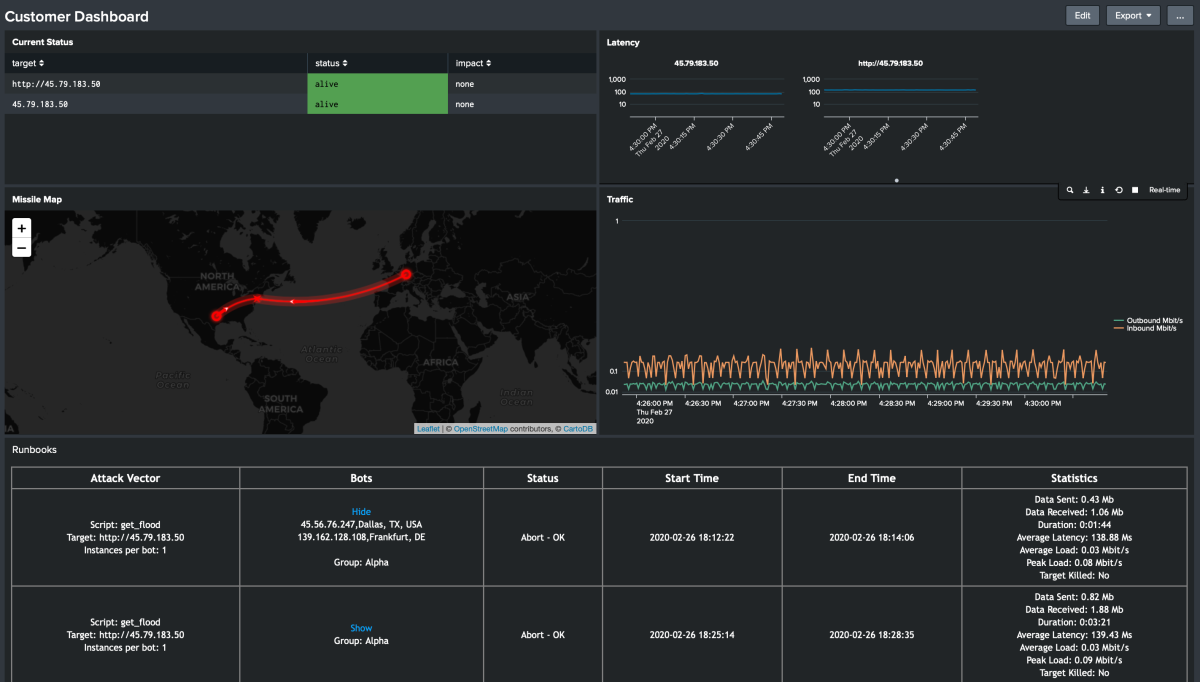
A live web dashboard will be available to you during the entire duration of the session. A multitude of real-time information is provided, such as the state of the target(s), insights into the traffic levels being sent and received, the number of attack bots available, and an overview of the current and previously executed attacks.
While you will get live insight via the dashboard into our actions and the results during the interactive attack session, you will also be provided with a report that will document the run-book, results, and recommendations on mitigating successful attacks. The report will contain details such as an explanation of the attacks, precise timelines of attacks, and witnessed impact to allow you to do post-mortem analysis. Additionally, each attack vector is supported by a graph that outlines the correlation between time and the response time of the system under attack. Most importantly, mitigation strategies and recommendations are offered to assist you in reducing the risk to your business.
Do you have any questions? Our experts are here to assist. Contact us!
Phone
BE: +32 3 3049512
NL: +31 (0)85 2736386

